Huge Android Botnet Steals Text Messages To Send To Chinese and South Korean Hackers
Earlier this month, we talked about the frustrating key-logger botnet call Pony, and it now appears that we couldn't make it through the rest of the month without having to discuss another. While the Pony botnet affected the PC, this latest one, dubbed Android.Spyware.MisoSMS by security firm FireEye, targets Android (as the name spoils).
At this point, it seems that MisoSMS affects those in China and Korea, which are the same countries the issuers of the malware also reside. MisoSMS disguises itself as an administrative app for Android, and even sports a believable Google icon. It's not clear how someone stumbles-upon this software, but it's not going to be found through official channels (eg: Google Play Store).
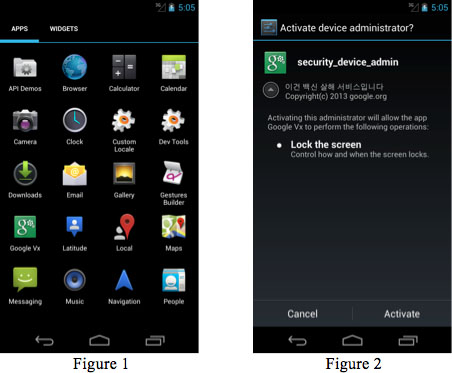
Once the app is opened, it seems that there's no way to proceed safely except to turn the phone off immediately. You'll be presented with a Cancel / Confirm question, and regardless of which one is pushed, the software initiates. In all, three separate services are installed, each one controlling a different portion of the malware.
Once active, MisoSMS will snag all of the SMS messages on your phone, store them in a database file, and email the result to a random temporary email address (which have all been disabled at this point). Should the send fail, the malware will simply try again later. With the sent information, not only is the SMS message itself included, but phone numbers are, as well.
FireEye believes that this malware is a perfect example for the need of cross-country and cross-organizational efforts to help take down these malicious botnets, or other security threats in general. I don't think anyone could disagree there.

