Android Exploit Leverages Lengthy Password Entry To Bypass Lock Screen
Updated
The lock screen on your phone might not be foolproof as you thought. Researchers at The University of Texas at Austin released a demonstration this week of what they say is a vulnerability in mobile devices running Android 5.x. Also known as Lollipop, it is the latest version of Android and is run by many modern phones, but the attack may not affect all phones running Lollipop. Researchers used a Nexus 4 in the proof-of-concept attack.
Also, phones running the latest version of Android (5.5.1 build LMY48M) are not vulnerable.
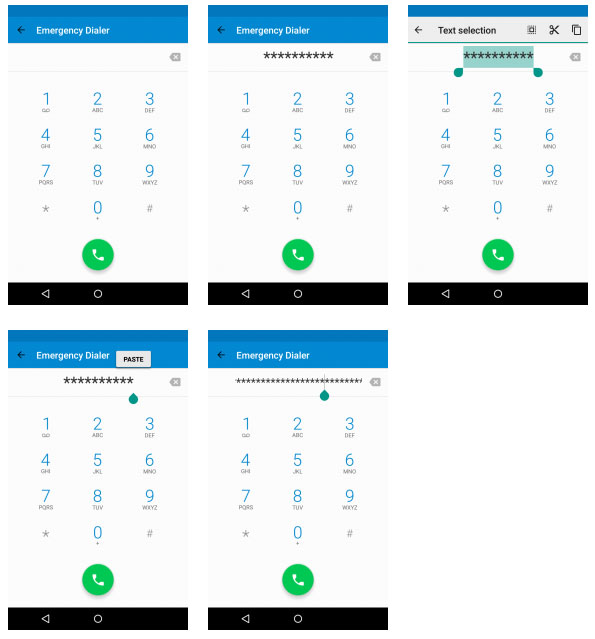
The attack involves copying and pasting multiple characters, starting with characters generated in the Emergency Dial section.
The “Elevation of Privilege Vulnerability in Lockscreen (CVE-2015-3860)” takes several minutes to complete. Researchers claim that by putting too many characters into the lock screen of the phone while the camera app is active, they can cause the lock screen to crash. That gives them full access to the phone’s home screen, even encryption is enabled on it.
The process is repetitive and makes for one of the more unexciting videos on the Internet. To open the phone, the attacker copies and pastes characters in the Emergency Dialer until he has a huge number of characters. Then he opens the camera app, followed by the password prompt. Then, he pastes the text string into the password field multiple times until the lock screen crashes and the camera app appears full screen. From there, he can enable USB debugging and use the Android Debug Bridge (ADB) tool to access files or issues commands.
As disturbing as the attack sounds, it’s not panic-worthy, for a couple reasons. For one thing, the issue was reported privately to Google and it issued a patch that solves the problem. As we mentioned earlier, if you have the latest version of Android, you’re safe.
And even if you are running a vulnerable version of Android (and on a vulnerable phone, at that), the attacker needs to have your device and have several minutes to perform the attack. Also, it appears that the hack works only with password-locked phones. If you use a pattern lock, for example, the attack shouldn’t affect your device.
The lock screen on your phone might not be foolproof as you thought. Researchers at The University of Texas at Austin released a demonstration this week of what they say is a vulnerability in mobile devices running Android 5.x. Also known as Lollipop, it is the latest version of Android and is run by many modern phones, but the attack may not affect all phones running Lollipop. Researchers used a Nexus 4 in the proof-of-concept attack.
Also, phones running the latest version of Android (5.5.1 build LMY48M) are not vulnerable.

The attack involves copying and pasting multiple characters, starting with characters generated in the Emergency Dial section.
The “Elevation of Privilege Vulnerability in Lockscreen (CVE-2015-3860)” takes several minutes to complete. Researchers claim that by putting too many characters into the lock screen of the phone while the camera app is active, they can cause the lock screen to crash. That gives them full access to the phone’s home screen, even encryption is enabled on it.
The process is repetitive and makes for one of the more unexciting videos on the Internet. To open the phone, the attacker copies and pastes characters in the Emergency Dialer until he has a huge number of characters. Then he opens the camera app, followed by the password prompt. Then, he pastes the text string into the password field multiple times until the lock screen crashes and the camera app appears full screen. From there, he can enable USB debugging and use the Android Debug Bridge (ADB) tool to access files or issues commands.
As disturbing as the attack sounds, it’s not panic-worthy, for a couple reasons. For one thing, the issue was reported privately to Google and it issued a patch that solves the problem. As we mentioned earlier, if you have the latest version of Android, you’re safe.
And even if you are running a vulnerable version of Android (and on a vulnerable phone, at that), the attacker needs to have your device and have several minutes to perform the attack. Also, it appears that the hack works only with password-locked phones. If you use a pattern lock, for example, the attack shouldn’t affect your device.

